IPv6 is not common yet, as most software, routers, modems, and other network equipment does not support the emerging and future-proof protocol yet. Beside, turning off IPv6 support does not affect the functionality of Internet browsing for average users. Thus IPv6 and/or Teredo can and (quite likely) should be disabled if it’s not in use to conserve system resources such as network bandwidth.
Unlike Windows XP, IPv6 in Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10 and their server equivalent or later cannot be uninstalled, according to Microsoft. However, IPv6 can be disabled. The following guide will allow users to disable IPv6 on a specific connection of a network interface card.
- Go to Network Connections folder (In Windows Vista, click on Start button, then go to right click on Network, select Properties, then click on Manager network connections on Tasks pane; In Windows 7, click on Start button, then go to Control Panel -> Network and Internet -> Network and Sharing Center, and select Change adapter settings on the right pane; In Windows 10, Windows 8.1 and Windows 8, open Win-X Quick Access menu, and select Network Connections.
- You should see various LAN, WAN, wireless, Bluetooth, high speed Internet, virtual Ethernet adapter, and other network connections available on the Windows computer with the network adapter description. Right click on the network connection that you want to disable the IPv6 interface and select Properties.
Click “Continue” or “OK” on User Access Control permission request prompt if applicable.
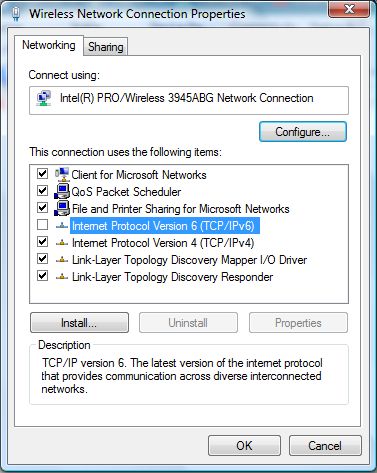
- Clear the check box next to the Internet Protocol version 6 (TCP/IPv6) component in the list under “This connection uses the following items” box.
- Click OK when done.
- To re-enable IPv6, tick back the check box.
This method disables IPv6 on the particular network interface and connection. For other network adapter or connection, users have to repeat the steps to disable IPv6. Beside, disable IPv6 on specific network connection also does not disable IPv6 on tunnel interfaces or the IPv6 loopback interface.
It’s also possible to disable IPv6 and/or Teredo via Windows system registry, which has the advantage to have the IPv6 policies applied to all network adapters. The registry settings also allow users to selectively disable components and configure behaviors for IPv6 in Windows operating system.
- Open Registry Editor (regedit).
- Navigate to the following registry key branch:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\tcpip6\Parameters\
- Create the following registry value (DWORD 32-bit Value):
DisabledComponents
Note that the name must be exactly as shown, including capitalization. DisabledComponents is set to 0 by default.
- The DisabledComponents registry value is a bit mask that controls a series of flags, starting with the low order bit (Bit 0). To determine the value of DisabledComponents for a specific set of bits, the process is complicated, where hexadecimal value is calculated from binary number of the bits in correct position. For convenient, the following table lists some common configuration combinations and the corresponding DWORD value of DisabledComponents.
Configuration combination DisabledComponents value Re-enable all IPv6 components 0 Disable IPv6 on all tunnel interfaces (Intra-Site Automatic Tunnel Addressing Protocol [ISATAP], 6to4, and Teredo) 0x01 Disable 6to4 0x02 Disable ISATAP 0x04 Disable Teredo 0x08 Disable Teredo and 6to4 0x0A Disable IPv6 on all nontunnel interfaces (LAN and PPP [Point-to-Point Protocol]) 0x10 Disable all IPv6 on all LAN, PPP and tunnel interfaces except for the IPv6 loopback interface. 0x11 Prefer IPv4 over IPv6 (change entries in the prefix policy table) 0x20 Disable all IPv6 components over all interfaces (except the IPv6 loopback interface) and prefer IPv4 to IPv6 0xFF As seen from table above, to disable IPv6 support globally on all interface, set the value data for DisabledComponents to 000000FF, or simply FF (in hexadecimal). The registry entry will look like below:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters] "DisabledComponents"=dword:000000ff
If you prefer to work with Command Prompt (running as Administrator), run the following command:reg add HKLM\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters /v DisabledComponents /t REG_DWORD /d 0x000000FF
Replace the value of 0x000000FF (with disable IPv6 totally) with applicable value that you prefer.
- Restart the computer for changes to take effect.
- To revert and enable IPv6, delete DisabledComponents registry key or set its registry value to 0.
Update: More ways available to disable Toredo for IPv4 and IPv6 bridge.