As a certificate authority can issue multiple certificates in the form of a tree structure, sometimes the intermediate CA certs issued by a so called subordinate certification authorities are essential to maintain the “chain of trust”. It ensures that the identity verification through the public key certificate can be performed and trusted properly, especially when establishing secure connection through Transport Layer Security (TLS) and/or Secure Sockets Layer (SSL). Otherwise, you may receive a warning that the certificate is signed by an “untrusted authority”.
Essentially, the root CA cert is used to sign and issue a certificate that in turn used to sign and issue end-entity or domain digital certificates for individual and company. Each digital certificate can have zero or more chains of CA certificates that extend back to the root CA cert.
Thus, you need to install the intermediate CA certificates in order for browsers to trust your certificate, if your certificate signing authority include an intermediate CA certificate or bundle (trust chain). In fact, most popular CAs use intermediate CA certs.
How to Get the Intermediate CA Certificate
Depending on the Certificate Authority, some CAs may email you a certificate bundles file which contains the intermediate CA certificates, or you can download the required Intermediate CA Certificate from the CAs’ repository. Some of the common CAs’ downloads repository are:
Comodo: https://support.comodo.com/index.php?/Default/Knowledgebase/Article/View/620/1/which-is-root-which-is-intermediate
GlobalSign: https://support.globalsign.com/customer/portal/topics/538410-root-certificates/articles
Symantec Verisign: https://knowledge.verisign.com/support/ssl-certificates-support/index?page=content&id=AR657
GoDaddy: https://certs.godaddy.com/repository
DigiCert: https://www.digicert.com/digicert-root-certificates.htm
StartCom StartSSL: https://www.startssl.com/certs/
TrustWave: https://ssl.trustwave.com/support/support-root-download.php
How to Install Intermediate CA Certificate (Chain Certificate)
- Copy the Intermediate CA Certificate in PEM format (a base64 encoded DER certificate identifiable with not meaningful text enclosed between “—–BEGIN CERTIFICATE—–” and “—–END CERTIFICATE—–“) to the server, and place in the same directory as the SSL certificate and private key files. For example, /home/techjourney/ssl/cert directory.
- Locate the following SSL directives in httpd.conf or ssl.conf or Apache configuration file that declares the SSL settings. Note that if you are using name-based Virtual Host via NameVirtualHost directive, you must locate the corresponding <:VirtualHost> segment that defines your domain website, and modify the SSL directives there (thanks for Server Name Indication (SNI), now you can host multiple SSL secure websites on a single IP address, as SNI allows client to indicate which hostname it is attempting to connect to at the start of the handshaking process).
Depending on the versions of your Apache, set the values of these SSL directives to the absolute path and filename of the various SSL certificates. If you already have SSL configured, you only need to concern about SSLCertificateChainFile or SSLCACertificatePath to install the intermediate CA certs.
In Apache version 2.4.7 or older (<= 2.4.7):
SSLCertificateFile Path to SSL certificate, e.g. /home/techjourney/ssl.cert SSLCertificateKeyFile Path to private key file, e.g. /home/techjourney/ssl.key SSLCertificateChainFile Path to intermediate CA cert or bundle, e.g. /home/techjourney/ca.bundle.pem In Apache version 2.4.8 or newer (>= 2.4.8):
SSLCertificateFile Path to SSL certificate, e.g. /home/techjourney/ssl.cert SSLCertificateKeyFile Path to private key file, e.g. /home/techjourney/ssl.key SSLCACertificatePath Path to intermediate CA cert or bundle, e.g. /home/techjourney/ca.bundle.pem NoteSSLCertificateChainFile is deprecated since Apache 2.4.8. In Apache 2.4.8, SSLCertificateFile was extended to also load intermediate CA certificates from the server certificate file. It means that if the signing Certificate Authority provides you the end-entity or domain certificate that also includes the intermediate CA certificates, you can omit the SSLCACertificatePath. - Save the Apache configuration file.
- Restart Apache:
service httpd restart
Or,
service apache2 restart
Or,
systemctl httpd restart
Or,
systemctl apache2 restart
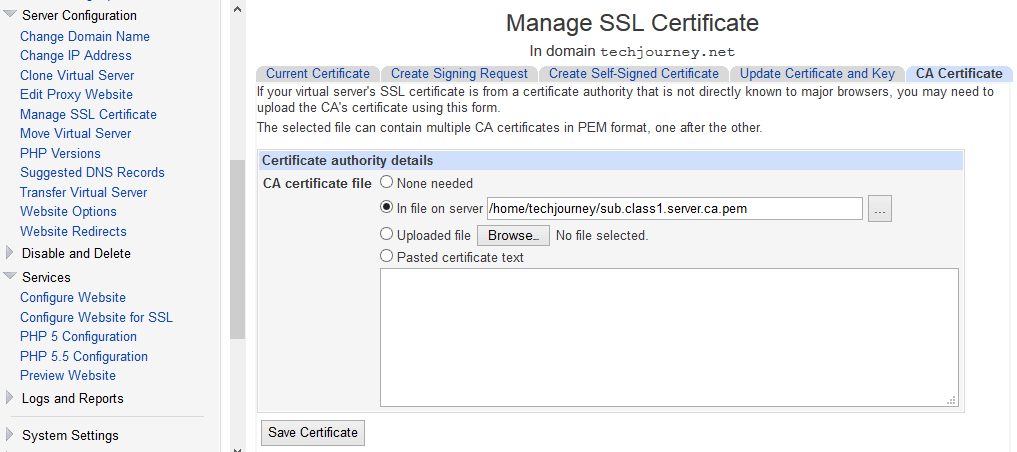
- Virtualmin: Select the virtual server (website or domain) if you have to install the intermediate CA certs. Then, go to Server Configuration -> Manage SSL Certificate -> CA Certificate. Select one of the way to provide the CA’s certificates, i.e. in a file on server if you already uploaded the CA’s certs to the host, uploaded file or pasted certificate text. Click Save Certificate when done, and the CA’s certs will be loaded via SSLCACertificatePath directive.
You can also manually edit the virtual server’s directives going to Services -> Configure Website for SSL -> Edit Directives, useful if you prefer the SSLCertificateChainFile directive to provide the intermediate CA certs.
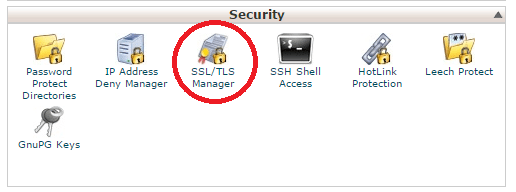
- cPanel WHM: Go to List Accounts on the left menu, and click on the cPanel symbol next to the host that you want install the intermediate CA certs.
At cPanel, select the SSL/TLS Manager under “Security”. Then, click on Manage SSL sites under “Activate SSL on Your Web Site (HTTPS)“. Select the appropriate domain name from the drop-down box. Then, paste the certificate into Certificate: (CRT) text box, paste the decrypted private key into the Key: (KEY) text box and paste the content of the CA certificates into the Certificate Authority Bundle: (CABUNDLE) text box. Hit Install Certificate when done.