To identify whether a private key is encrypted or not, open the private key in any text editor such as Notepad or Notepad++. An encrypted key has the first few lines that similar to the following, with the ENCRYPTED word:
—–BEGIN RSA PRIVATE KEY—–
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-256-CBC,AB8E2B5B2D989271273F6730B6F9C687……………………………………………….
……………………………………………….
………………………………………
—–END RSA PRIVATE KEY—–
On the other hand, an unecrypted key will have the following format:
—–BEGIN RSA PRIVATE KEY—–
………………………………………..
………………………………………..
…………………………………..
—–END RSA PRIVATE KEY—–
Encrypted key cannot be used directly in applications in most scenario. It must be decrypted first.
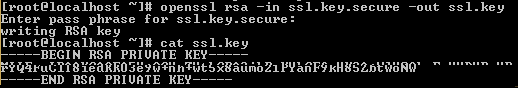
OpenSSL in Linux is the easiest way to decrypt an encrypted private key. Use the following command to decrypt an encrypted RSA key:
openssl rsa -in ssl.key.secure -out ssl.key
Make sure to replace the “server.key.secure” with the filename of your encrypted key, and “server.key” with the file name that you want for your encrypted output key file.
If the encrypted key is protected by a passphrase or password, enter the pass phrase when prompted.
Once done, you will notice that the ENCRYPTED wording in the file has gone.
If a private key or public certificate is in binary format, you can’t simply just decrypt it. To convert from X.509 DER binary format to PEM format, use the following commands:
For public certificate (replace server.crt and server.crt.pem with the actual file names):
openssl x509 -inform DER -outform PEM -in server.crt -out server.crt.pem
For private key (replace server.key and server.key.pem with the actual file names):
openssl rsa -inform DER -outform PEM -in server.key -out server.key.pem
For public certificate (replace server.crt and server.crt.pem with the actual file names):
openssl x509 -inform PEM -in server.crt > server.crt.pem
For private key (replace server.key and server.key.pem with the actual file names):
openssl rsa -in server.key -text > server.key.pem