Hash value, or hash checksum, for a file is commonly used to verify the integrity of the file, especially on large files downloaded over the Internet where the downloads are corrupted or may not be completed properly and fully. Hash value is a distinct and unique value that is assigned to the contents of a file, and hash value stays constant and is not changed even though file name and/or file extension is changed as long as file content is not altered in any way.
Thus, hash checksum provides a cryptographically-secure way to verify that the contents of a file have not been changed. Any changes to the content, even though just a single character, changes the hash value of the file, even though the file name or extension stays the same. By comparing the hash value of the file against the officially published hash value, one can determine if the file is exactly the same and identical with the original, intact, genuine, unmodified, untouched, not corrupt, and usable.
There are plenty of utilities available that can calculate the hash value or hash checksum for files. If you’re using Windows operating system, you can also use the PowerShell built-in cmdlet to computer the hash value for a file, without the need to install any additional software.
The PowerShell cmdlet to computer the hash value by using a specified hash algorithm is Get-FileHash, with the following syntax:
Parameter Set: Path or LiteralPath
Get-FileHash {[-Path] | -LiteralPath} <String[]> [-Algorithm <String> {SHA1 | SHA256 | SHA384 | SHA512 | MACTripleDES | MD5 | RIPEMD160} ] [ <CommonParameters>]
Parameter Set: Stream
Get-FileHash -InputStream <System.IO.Stream> [ <CommonParameters>]
To use the Get-FileHash cmdlet, open a PowerShell window by searching for it in Start Search, and then run the command. For example,
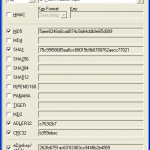
PS C:\> Get-FileHash C:\Users\TechJourney\Downloads\Windows10.ISO | Format-List
If no algorithm is specified, the Get-FileHash cmdlet uses the SHA256 algorithm by default. Any hash algorithm that is supported by the operating system can be used. In the command above, The output is piped to the Format-List cmdlet to format the output as a list.
To specify another algorithm, use the -Algorithm switch. For example,
PS C:\> Get-FileHash C:\Users\TechJourney\Downloads\Windows10.ISO -Algorithm MD5 | Format-List
The following cryptographic hash algorithm functions are supported:
- SHA1
- SHA256
- SHA384
- SHA512
- MACTripleDES
- MD5
- RIPEMD160
For security reasons, MD5 and SHA1, which are no longer considered secure, should only be used for simple change validation, and should not be used to generate hash values for files that require protection from attack or tampering.